Cybersecurity
The company realizes that information technology systems have played an increasingly important role in the company's operations. This is in line with the continuous growth and expansion of the company's business to prevent unauthorized access to information or use of information and systems by users and various forms of threats. The company has guidelines for controlling the security of information technology systems. By preparing an operational plan announcement of policy and having a clear work process. There is internal and external communication with relevant agencies to inform them about information technology system security management in accordance with laws and various practices, including operations that meet international standards, to ensure that the company's information is protected and to build confidence and trust among all stakeholders.
The company has established a working group on information technology security, consisting of the Executive Chairman and executives from various related departments. The group has the following structure:
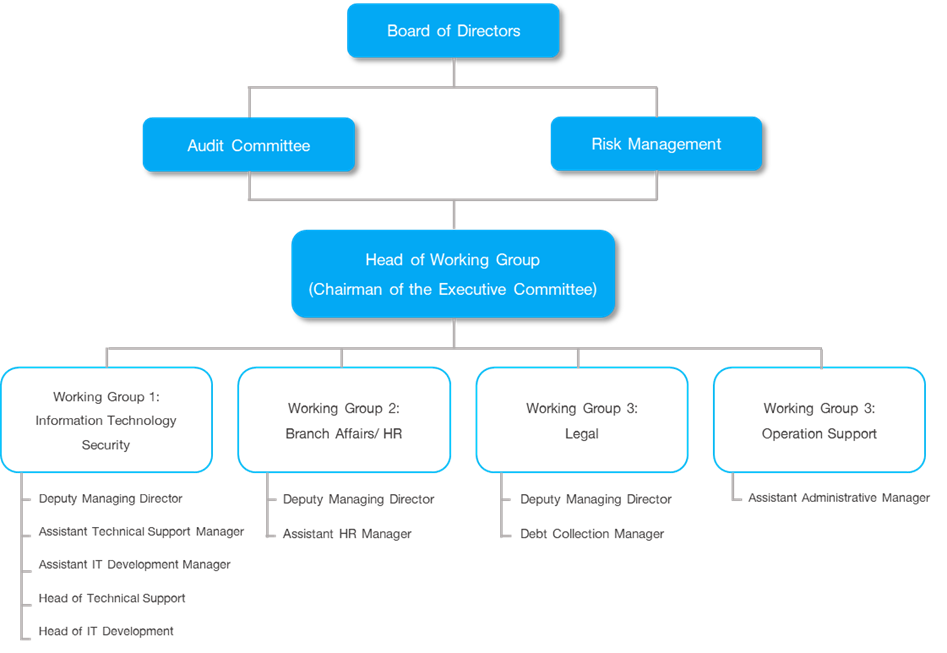
Role and Responsibility
- The Board of Directors is responsible for approving policies and measures to maintain the security of the information technology system, prioritizing prevention of issues stemming from inappropriate network usage and threats from users and other sources.
- The Information Technology System Security Working Group, Lead by the Executive Chairman, oversees security operations to ensure compliance with legal and regulatory requirements, assessing information risks under risk management supervision.
- Employees are obligated to adhere to policies, regulations, directives, and operational manuals concerning information system security measures.
The working group is tasked with overseeing information system security operations to align with relevant standards and laws, implementing corrective and preventive measures, and enhancing operational efficiency. The company ensures that operational results are reported to the Audit Committee and Risk Management Committee at least once a year.
Management Apporach
- Installation of network security software (Firewall) to prevent data leakage from external attacks computer viruses.
- Determination and enhancement of access authority to prevent information leakage.
- Implementation of a data backup plan and regular checks to ensure compliance with the information security policy.
- Internal communication initiatives to raise awareness among employees regarding the proper and secure use of technology.
- Development of a manual for protecting personal information and information security, along with the establishment of a Business Continuity Management Plan (BCP) to address interruptions in business operations caused by IT system threats.
- Engagement of an external IT Auditor to evaluate internal controls and manage IT system risks, with audit results reported directly to the Audit Committee and the Risk Management Committee.
Year in review
The company conducted two rehearsals of the information systems recovery plan to test the emergency response plan. An external agency reviewed the IT control systems, focusing on access management and data security. After the review, the findings and recommendations were discussed with management to refine policies and improve the company’s processes for greater security and efficiency. The company also promotes cybersecurity awareness among employees through training provided by external agencies and encourages them to stay informed about technology and cyber threats via internal communications. In 2024, the company did not encounter any information security incidents.


